Central-February
Wednesday, February 3, 2021
Virtual
Keynote Speaker
“The Human User is the New Endpoint”
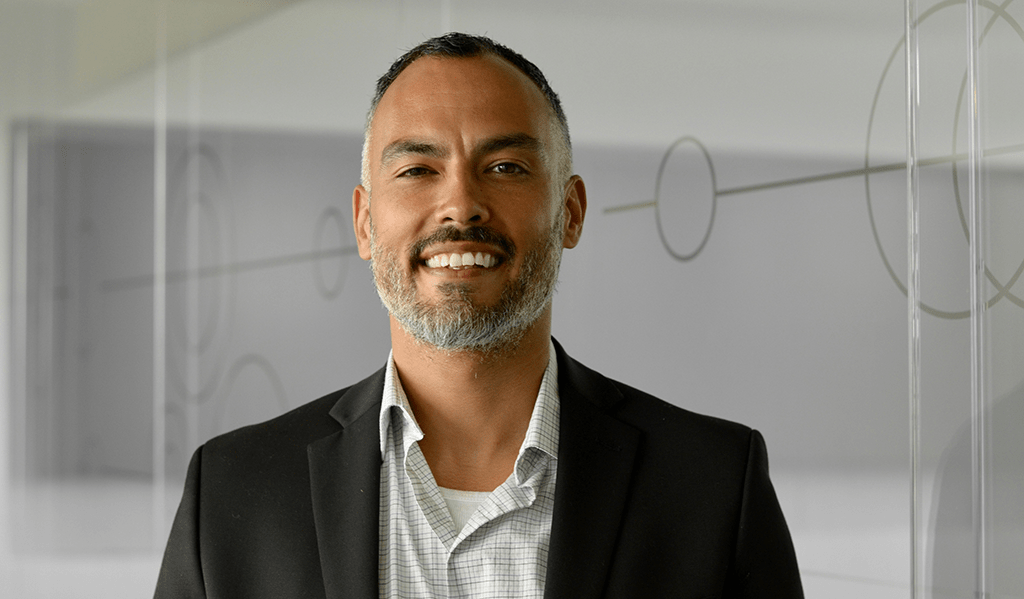
Otavio Freire
CTO and Co-Founder SafeGuard Cyber
Don’t Miss This Keynote—A Global leader in the CyberSecurity Industry:
- Who's, Who of Cyber Security- Onalytica
- Advisor to the European Commissioner for the Security Union
- Briefed the EU Parliament on Disinformation Operation Tactics that threatened the EU elections
- Briefed US Senate on Digital Risk staffers face
- Security advisor to the EEAS (European Union External Action Service)
- Uncovered a massive operation against EU Elections reported by the Guardian
- Uncovered attacks that have been reported by Washington Post, BBC, LeFigaro, Politico, Epoch Times, NBC, Sputnik, Forbes, Bloomberg, and all the major cyber magazines. Serves major Fortune 100 Enterprises and well-known political office holders on the digital security
CISO/Industry Leader Panel
CISO Panel: Hear from cybersecurity leaders and experts on current cyber threats and practices
Laureen Smith
Executive - Cybersecurity Advisory LJ Marketing & Communications
Jonathan Kimmitt
Chief Information Security Officer, Alias Cybersecurity Former CISO The University of Tulsa
Jason Lewkowicz
Global Chief Information Security Officer Cognizant
Mike Raeder
Deputy Chief Information Security Officer, Director Information Security Northrop Grumman
About the Event
FutureCon Events brings high-level Cyber Security Training discovering cutting-edge security approaches, managing risk in the ever-changing threat of the cybersecurity workforce.
Join us as we talk with a panel of C-level executives who have effectively mitigated the risk of Cyber Attacks.
Educating C-suite executives and CISOs (chief information security officers) on the global cybercrime epidemic, and how to build Cyber Resilient organizations.
“Cybersecurity is no longer just an IT problem”
Gain the latest knowledge you need to enable applications while keeping your computing environment secure from advanced Cyber Threats. Demo the newest technology, and interact with the world’s security leaders and gain other pressing topics of interest to the information security community.
The FutureCon community will keep you updated on the future of the Cyberworld and allow you to interact with your peers and the world’s security leaders.
For sponsorship opportunities email sales@futureconevents.com
Agenda
Times are subject to change
Opening Introductions
Sponsor Booth Networking Time
Presentation
CIAM in an uncertain world
In today’s uncertain world, organizations must find ways to ensure their customers can engage with their services at any time, from any device, in a secure and safe manner. That is where customer identity and access management comes in or “CIAM”. A CIAM solution must not only meet today’s security and compliance standards, but also create frictionless customer experiences to meet customers where they are and in the ways they need. Join our sessions as we discuss CIAM in more detail, how priorities have shifted this year and what CIAM maturity looks like.
Sponsored by

Presentation
Extortionware: Your Privacy Problems Made Public
Over the last decade, ransomware has increasingly become the most popular option for hackers to monetize the access they’ve obtained to corporate computer systems around the world. Over the last few years, we’ve observed ransomware software and techniques adapt and evolve to include the theft and exposure of private information, creating extortionware as a new breed of malicious software. This talk will provide an overview of these techniques and discuss the potential privacy and security impacts you may face as a result.
Sponsored by

Keynote
The Human User is the New Endpoint
Today’s Boards’ task us with ensuring good governance that drives growth.
This must include compliance and cybersecurity, especially regarding the new, unprotected cloud channels that drive business in today’s unpredictable work-from-anywhere paradigm. Channels like LinkedIn and Twitter are now mission-critical for executive leaders. Others like WhatsApp and WeChat may be necessary to ensure uninterrupted business communication with contacts in overseas markets. These apps are vulnerable, and this should worry boards everywhere.
Although the new generation of digital channels is very popular, the security solutions are lagging. No firewall or email filter can protect a LinkedIn inbox. Most security teams possess no tools to protect their cloud channels, which live outside the traditional security perimeter. Add to this complexity, the portability of these channels both on desktop and mobile devices, frequently accessed outside of VPN structures. The human user is the new endpoint and its not just about hacking the physical structure but “perception hacking” of those users.
Otavio Freire, CTO & Co-Founder of SafeGuard Cyber, will share recent high profile examples of social engineering attacks along with ways we can protect our companies and provide assurances at the board level.
Live Presentation
Conquering Cyber Risk in 3rd Party Communications
The Enterprise Content Firewall
To do their jobs, employees must share IP, PII, PHI, and all means of sensitive content with customers, suppliers, partners and a broad ecosystem of trusted 3rd parties. However, they put the organization at risk when they communicate across untrusted devices, networks, applications and identities. How can you prevent beaches and compliance violations from everyday 3rd party communications when you can’t even see what’s going on? This session explores the need for a next-generation “content firewall” that rises above packets and traffic to inspect content and communication, and thereby ensure confidentiality, compliance and control of risky 3rd party business processes.
Sponsored by

Live Panel Discussion
CISO Panel: Hear from cybersecurity leaders and experts on current cyber threats and practices
Hear from cybersecurity leaders and experts on:
- Current cybersecurity threats and practices
- Post-pandemic security
Jonathan Kimmitt
Chief Information Security Officer, Alias Cybersecurity Former CISO The University of Tulsa
Mike Raeder
Deputy Chief Information Security Officer, Director Information Security Northrop Grumman
Sponsored by

Are you ready for Intelligent SOC?
Sponsored by

Presentation
Past, Present, Future: Zero Trust Architecture
In this webinar you will learn:
- How to maximize existing security controls, security capabilities, and investments
- Pragmatic application of zero-trust principles to traditional and SaaS environments
- What’s new in tactics and strategies for protecting hybrid environments
Data breaches grab headlines. Good security is steady. As organizations expand their perimeter beyond the firewall through software-as-a-service (SaaS) and hybrid applications, it becomes more important than ever to have a strategy covering user access regardless of location. But alongside developments in new tools, data privacy laws have also developed and add to compliance requirements for managing these data and tool. Meanwhile, modernization efforts are introducing new risks as well. While many industries have adopted zero-trust strategies to address these challenges of the expanded perimeter, many admins remain wary of this trend and question if it is a fit for environments which often have a hefty legacy technology footprint.
However, many of these “new” strategies remain firmly rooted in tried-and-true best practices admins have followed for decades. The principles of logical segmentation, least-permissive access, economy of mechanism, adaptive policy controls, and strong authentication are simply evolving to accommodate new use cases rather than being replaced. Join this session with Duo Security Advisory CISO Wolfgang Goerlich for a grounded discussion of the unique needs and concerns for modern IT teams based on real-world examples, and how concepts like device trust and context-aware access can improve security design without leaving crucial inherited or legacy systems out in the cold.
Sponsored by

Presentation
Supply Chain Compromise
Supply chain cybersecurity risk warnings increased by 80% by Q2, 2020, and this trend is likely to continue. During this webinar, Jamie Hart will cover:
– Overview of supply chain compromise and third party risks
– Historical supply chain attacks
– Common tactics, techniques an procedures
– Mitigation options
Sponsored by

Presentation
Stay Ahead of the Hacker with Continuous Security Testing
Join Sion Retzkin, CISO & Head of Knowledge & Practice, Pcysys to learn how to:
-
Build up your cyber resilience with continuous risk validation
-
Prioritize remediation efforts with a threat-facing perspective
-
Increase the productivity of your security teams
Sponsored by

Presentation
Review of The Most Widely Used Malicious Command & Control Infrastructure
Malicious command and control families and tools can be tough to keep an eye on. Identifying and monitoring suspicious servers is a tall order. Sometimes “suspicious” hosting providers can turn out to be false positives, and servers that seem innocuous can pose a greater threat than you’d imagine. In this session, Recorded Future has some fresh insight to keep you up to speed. This will include a first-look at the novel indicators and intelligence not otherwise available in the public domain. Get an inside look into:
- Key 2020 findings related to over 10,000 unique command and control servers, across more than 80 families
- Best practices for proactive detection, ongoing monitoring, and defense-in-depth approaches to adversary infrastructure
- The 2021 outlook for C2s, and what you can do to stay ahead
Sponsored by

Presentation
Self-learning AI that protects your workforce
Sponsored by

Presentation
How to Detect Common Threats Targeting Your Cloud Infrastructure
Join Amanda Berlin, Sr. Incident Detection Engineer at Blumira for a discussion on common cloud security detections and how to detect threats targeting your cloud infrastructure.
In this talk, you’ll learn about:
- Different types of attacks targeting cloud infrastructure platforms like Microsoft Azure, Office 365, Okta, G Suite and Amazon Web Services
- Common vulnerabilities that may lead to a compromise
- How to properly detect cloud-related misconfigurations and potential threats to reduce your overall attack surface
Sponsored by