Dallas, TX (Western Region)
Wednesday, March 3, 2021
Virtual
Keynote Speaker
““2020 is in hindsight, are we ready for what’s ahead?””
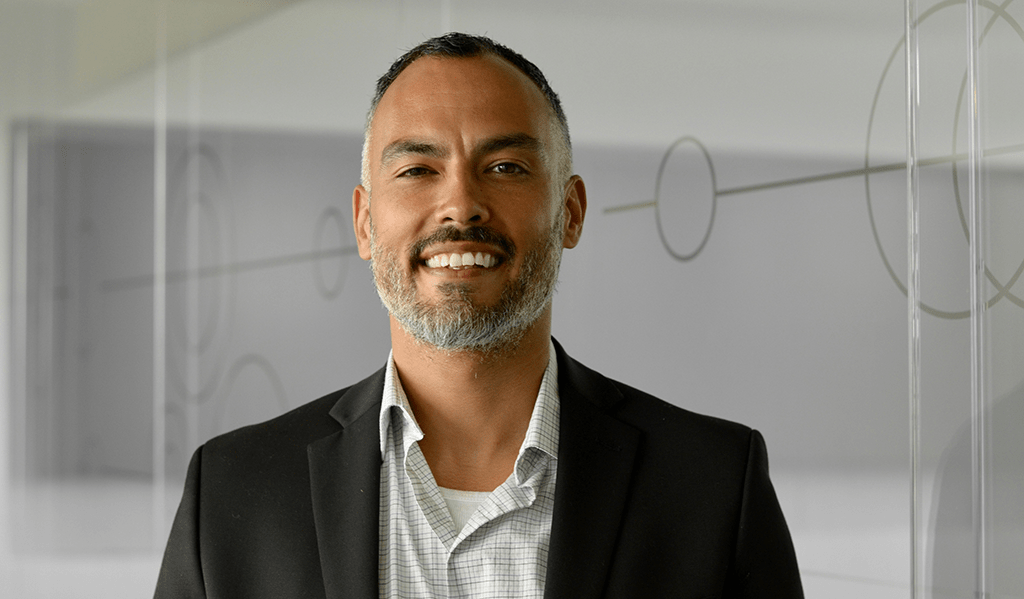
Sujeet Bambawale
Chief Information Security Officer 7-Eleven
CISO/Industry Leader Panel
CISO Panel: “When your supply chain becomes a kill chain – Managing third-party risk”
Eric Yancy
Information Security Officer City of Irving
Scott Smith
Chief Information Security Officer City of Bryan
Kevin Joyner
Chief Information Security Officer Brazos County
David Belanger
Chief Security Officer Bestow
Jeff Murray
Protective Security Advisor U.S. Department of Homeland Security
About the Event
FutureCon Events brings high-level Cyber Security Training discovering cutting-edge security approaches, managing risk in the ever-changing threat of the cybersecurity workforce.
Join us as we talk with a panel of C-level executives who have effectively mitigated the risk of Cyber Attacks.
Educating C-suite executives and CISOs (chief information security officers) on the global cybercrime epidemic, and how to build Cyber Resilient organizations.
“Cybersecurity is no longer just an IT problem”
Gain the latest knowledge you need to enable applications while keeping your computing environment secure from advanced Cyber Threats. Demo the newest technology, and interact with the world’s security leaders and gain other pressing topics of interest to the information security community.
The FutureCon community will keep you updated on the future of the Cyberworld and allow you to interact with your peers and the world’s security leaders.
For sponsorship opportunities email sales@futureconevents.com
Agenda
Times are subject to change
Opening Introductions
Networking
Sponsor Booth Networking Time
Presentation
Past, Present, Future: Zero Trust Architecture
In this webinar you will learn:
- How to maximize existing security controls, security capabilities, and investments
- Pragmatic application of zero-trust principles to traditional and SaaS environments
- What’s new in tactics and strategies for protecting hybrid environments
Data breaches grab headlines. Good security is steady. As organizations expand their perimeter beyond the firewall through software-as-a-service (SaaS) and hybrid applications, it becomes more important than ever to have a strategy covering user access regardless of location. But alongside developments in new tools, data privacy laws have also developed and add to compliance requirements for managing these data and tool. Meanwhile, modernization efforts are introducing new risks as well. While many industries have adopted zero-trust strategies to address these challenges of the expanded perimeter, many admins remain wary of this trend and question if it is a fit for environments which often have a hefty legacy technology footprint.
However, many of these “new” strategies remain firmly rooted in tried-and-true best practices admins have followed for decades. The principles of logical segmentation, least-permissive access, economy of mechanism, adaptive policy controls, and strong authentication are simply evolving to accommodate new use cases rather than being replaced. Join this session with Duo Security Advisory CISO Wolfgang Goerlich for a grounded discussion of the unique needs and concerns for modern IT teams based on real-world examples, and how concepts like device trust and context-aware access can improve security design without leaving crucial inherited or legacy systems out in the cold.
Sponsored by

Live Presentation
SolarWinds Breach and Ransomware in 2021
We’ll discuss how to gain visibility into your environment and vulnerabilities to detect them early and effectively and expand your defense beyond the perimeter through XDR to stay prepared for the next breach. Because it’s not if you get breached, it’s when.
What you’ll learn:
- How hackers used highly evasive malware to compromise SolarWinds defenses.
- Assessing your environment and determining vulnerability.
- Finding and addressing lateral movement in your environment.
Snehal Contractor
Vice President Worldwide Systems Engineering & Technical Services Stellar Cyber
Sponsored by

Live Keynote
“2020 is in hindsight, are we ready for what’s ahead?”
Live Presentation
Cyber-security in the AGE OF THINGS
Cybercriminals are taking advantage of the increase in remote workers due to the coronavirus, by increasing their attacks on IoT devices. Given 63% of enterprises, 92% of industrial organizations, and 82% of health care organizations use IoT, almost every company is exposed. Unfortunately, connecting IoT devices to the network extends the attack surface providing more entry points for hackers.
Join the session to learn how to prevent IoT cyber-attacks by:
- Exposing all IoT security risks across IT and OT networks
- Easily creating policies to secure thousands of IoT devices
- Preventing both network-based and device-level attacks
Sponsored by

Live Panel Discussion
CISO Panel: “When your supply chain becomes a kill chain – Managing third-party risk”
Presentation
How Cyber AI Detects Digital Fakes and Impersonation Attacks
Today, 94% of cyber-threats still originate in the inbox. ‘Impersonation attacks’ are on the rise, as artificial intelligence is increasingly being used to automatically generate spear-phishing emails, or ‘digital fakes’, that expertly mimic the writing style of trusted contacts and colleagues. Humans can no longer distinguish real from fake on their own – businesses are increasingly turning to AI to distinguish friend from foe and fight back with autonomous response. In an era when thousands of documents can be encrypted in minutes, ‘immune system’ technology takes action in seconds – stopping cyber-threats before damage is done. Find out how in this session.
Sponsored by

Presentation
Talking to the Board About the New Realities of IT Security
When attacks make headlines, panicked board members have one question for CISOs: how can we be sure that won’t happen to us? CISOs must be prepared to lead board-level conversations about risk management amidst the stark new realities of IT.
Join this virtual boardroom to discuss:
- Achieving alignment across the board
- Building a “roadmap to yes”
- Focusing on risk and reward for core business objectives
Sponsored by

Presentation
Rational Approach to Zero Trust
Sponsored by

Presentation
Are you ready for Intelligent SOC?
Sponsored by

Presentation
Extortionware: Your Privacy Problems Made Public
Sponsored by

Presentation
Stay Ahead of the Hacker with Continuous Security Testing
Join Sion Retzkin, CISO & Head of Knowledge & Practice, Pcysys to learn how to:
-
Build up your cyber resilience with continuous risk validation
-
Prioritize remediation efforts with a threat-facing perspective
-
Increase the productivity of your security teams
Sponsored by

Presentation
Making the SOC more effective by enabling automation with better data
SOAR has been pitched to the industry as a way to resolve alert fatigue by automating common analyst workflows. Experience shows, however, that automation is only as good as the data that underlies it – so many people avoid SOAR, because of the complexity of getting “ready” for it. This talk will discuss open source Zeek as an approach for simplifying the acquisition of network data that’s directly applicable to SOAR, and the application of it through open source playbooks being released by Corelight.
Sponsored by